| |

What is a Firewall?

A
firewall is used to keep the internal network
segment secure
from intruders. It was develop by Sun
Microsystems and CheckPoint Software Technologies .
What
does a Firewall do?

A firewall ensures that
all packets coming into the internal network
does not consist of malicious contents. This
is done by inspecting each packet and decides,
based on your rules, whether they should be allowed.
It helps to prevent hackers break in and filter
email viruses. To protect trusted networks from
invasion, many firewalls are deployed at either
the network level or on the PC.
Why do we need a Firewall in a business environment?

Every business nowadays relies on Internet to
retrieve the latest information and establish
a competitive advantage. Firewall helps business
to protect their intangible assets, while monitoring
Internet usage.
Figure: Firewall

|
|
| |
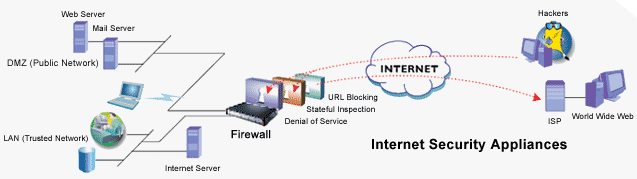
How does a Firewall work?

There are three technologies built on a firewall,
they are Packet Filtering, Application Layer
Gateways and Stateful Inspection.
Denial
of Service (DoS)

All
of the varieties of hacker attacks, we introduce
the more common
ones here: Denial of Service (DoS)
Denial
of Service is a type of attack on a network
that is designed to bring the network to
its knees by flooding it with useless traffic.
The servers will be so busy accepting or
denying requests and thus cannot provide
normal services to legitimate users. Many
DoS attacks, such as the IP Spoofing, Ping
of Death, SYN Flood and Teardrop attacks,
exploit limitations in the TCP/IP protocols.
The
three common DoS attacks

IP
SpoofingˇGA technique used to gain
unauthorized access to computers, whereby the
intruder sends messages to a computer with an
IP address indicating that the message is coming
from a trusted host. To engage in IP spoofing,
a hacker must first use a variety of techniques
to find an IP address of a trusted host and then
modify the packet headers so that it appears
that the packets are coming from that host.
Ping of DeathˇGAttacks
operating systems that fail to handle packets
that are larger than their acceptable sizes.
This is done by ˇ§pingingˇ¨ the target computer
with an illegitimate size packet i.e., over 65535
bytes in size). This will make the operating
system hangs when it tries to respond to it.
Teardrop ˇG This
attack relies on system vulnerability that causes
many systems to crash when they receive IP packets
that have been corrupted so that the data overlaps.
Teardrop attack exploits weakness in the reassemble
of the IP packet fragments. As data is transmitted
through a network, IP packets are often broken
up into smaller chunks. Each fragment looks like
the original packet except that it contains an
offset field. The Teardrop program creates a
series of IP fragments with overlapping offset
fields. When these fragments are reassembled
at the destination, some systems will crash,
hang, or reboot |
|







